Worldcoin and xx Network postage
DISCLAIMER: this is not investment advice. I've no idea what will happen and I don't recommend anything.
Introduction
xx Network has been around for years and has users, but not very many because:
- many Web3 and coin projects suffer from Not Invented Here syndrome (example)
- many projects don't know about xx Network
- several smart projects know and appreciate xx Network but they're are still in the process of integrating with xx Network (or the other way around)
Worldcoin is one of those smart projects in "the other way around" situation - xx Network is creating integrations for Worldcoin and this is work in progress (and progressing well).
Specifically, there are three Worldcoin Foundation grants that were awarded to xx Network-affiliated developers. You can read or listen about it in this interesting interview with one of the developers.
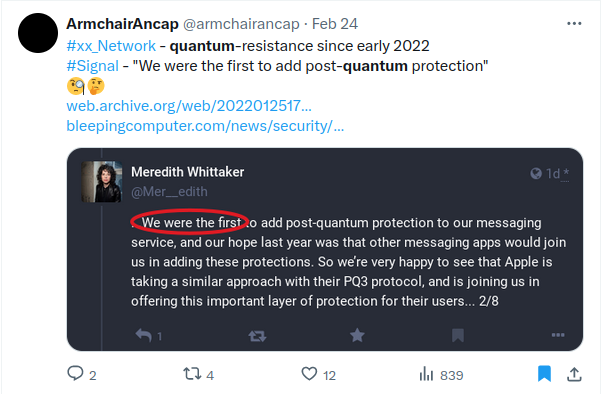
Meanwhile, Worldcoin is doing their thing. Today I saw this:
MIMOS Berhad, the applied research and development arm of the Malaysian Government, has signed an MoU with the Worldcoin Foundation, Tools for Humanity (TFH) and MyEG, a leading e-government services provider, to integrate Worldcoin technology into the country’s digital infrastructure.
The intent of the MoU is to leverage the Worldcoin protocol and TFH technologies to improve ongoing and future work related to digital credentials. In doing so, it validates the importance of digital proof of humanness in the age of AI.
Hmm, wait, how many people live in Malaysia? 34 million.
Whoa - xx coin will go to the moon!!!
No, it won't. But fine - let's talk about postage!
Postage
I've blogged about "postage", which is how xx Network plans to charge for its Premium tier suitable for power users.
Where will the collected postage go? Mostly to the validators - server operators on xx Network - and (if I recall correctly) part of it goes to the xx Foundation.
Does that mean that the price of xx coin will moon? Of course not.
We don't know if those Worldcoin apps in Malaysia will actually be released. It's just an MoU.
Even if they make it, we don't know if they'll choose to use Worldcoin's privacy features that rely on xx Network. The Malaysian integrators could choose to not use them at all and I'd say this may be the most likely outcome in this particular country.
We don't know how many apps will be developed, and how frequently they'll be used.
We also don't know if the apps will need access to Premium tier. Each individual user probably won't need it and postage measures access by each individual user. An app can have 5 million users and as long as each sends or receives several messages per minute, none of them will need to pay postage.
Are the chances of Worldcoin apps using xx Network's Premium tier nil, then?
Why pay postage
While only a very small percentage of Worldcoin (or other platform's) users will require access to Premium (or "unlimited" aka "best effort") tier, anyone who charges for their application or service or wants to prevent another paying user (or all the free users) from hogging them out, may want to ask users to subscribe to the Premium tier if it's affordable enough.
I'm not making this up to spread the idea that massive demand for xx coin is inevitable or just around the corner.
What I'm saying is I expect postage will be inexpensive enough to be purchased for "just in case" situations.
When you think about it, that's almost the opposite from "xx coin will moon" - the idea here isn't to create scarcity and get rich off the appreciating xx coin. On the contrary!
The way markets work is: if you want more of something, you pay for it just enough to make the seller willing to satisfy that demand.
If xx Network's message mixing service (cMix) works well for you, there's no "reason" to pay anything. (But you have the option to donate to the Foundation if so inclined).
But the presence of a Free Tier also means that everyone gets the same rights.
Someone can stand up 500 containers in AWS and spam the network all day long just because. Or simply try to freeload as much as possible.
If this happens at scale, quality of service as experienced by Free tier users may be impacted.
If you are getting paid for the app you sell or rely on xx Network at scale, then it may be wise to avoid such congestions where a busy day for Free tier users translates into a busy day for your Support staff. It's better to pay some postage just in case of accidental or malicious congestions.
As users pay for Postage, decentralized nodes that participate on the network ("validators") earn more xx coins which means more nodes can come online without diluting any node's daily earnings and at the same time improves network throughput.
Demand for xx coin may result in its price going up, but I would not expect significant impacts from demand for postage because as long as similar services exist, no one will pay 3x premium for xx Network. They may pay a 10% or even 110% more, but not for very long.
In addition to this "just in case I need it" scenario, there may be high volume users who prefer to use Premium tier on a regular basis.
A power user who sends thousands of messages every day (example: IoT feed or remote camera that chunks images into many "text" messages) could set up multiple identities to stay within the Free tier limit, or make his life simpler and pay a small premium for 1-2 thousand messages above the cut-off message limit for the Premium tier.
How will postage work? You may view a draft of high-level design for v1.0 features here.
As you can see in that document, users will also be throttled per smaller units of time, so that no one can overload the network by exhausting their daily quota within 15 minutes.
We can also see that in v1.0 there will be no "reserved capacity" which some users would probably like to have. Examples:
- Elections: with 5 million voters and (only) 3 hours to vote, you may want to prepay for 600 messages per second during voting hours on the election day. xx Network would then lower its Free tier throughput from (let's say) 7 to 5 messages per client per minute and drop total Free tier throughput per second by 600 messages per second. But this isn't easy. We may need smart contracts (to reserve time) which Polkadot SDK has, but xx Network hasn't yet activated on its Substrate-based xx chain. And there's another problem: speculators could front-run legitimate buyers as election dates are known in advance and often hard-coded in legislative acts
- Any user with "guaranteed minimum" requirements. Even if you need to send just 1 message per minute (which well within the Free tier - there's 1,440 minutes in a day) - you may want to pay postage in order to able to send at least one message per minute
When you consider all these niche scenarios, it's easy to see how this gets complicated quickly. I've no idea what's the best way to go about it in Postage v2 or later, but for thousands of users with custom requirements, Smart Contracts maybe the way to go as all mixing nodes can easily look them up on xx chain.
Node operators and permissionless postage
If you need guaranteed throughput for your clients, you can strike a deal whereby an operator gives you a dedicated, guaranteed fraction of their node's connections. You'd have to approach them on xx Network Discord and so on, but in theory that's possible.
No one needs to know, you get guaranteed throughput when everyone else may be timing out while connecting to xx Network gateways. Can that be done?
Not for very many messages and users, but it's certainly viable for either Free or Premium tiers. I can reserve 10kB/s for your client IP or throttle everyone else but your IP, for example.
Any node operator could make such side deals on their own for users who don't mind to always connect to the same gateways. That decreases user's privacy, so that's a trade-off which may or may not matter.
Another trade-off is if the network is overloaded, that node may be able to accept your messages just fine, but still unable to complete mixing them with other (random) groups of nodes out there, so it's not guaranteed to work in terms of actually sending messages.
I conclude this would be possible but not very valuable for either the node operators ("validators") or users. The Premium Tier is expected to be cheap enough to make these laborious workarounds unnecessary and unattractive financially, technically, and privacy-wise.
One use case for this may be local elections, where the government stands up 3-4 nodes and limits access to in-country IPs. As noted above that would impact - maybe even compromise (I'm not qualified to tell) - privacy, but not the integrity of messages (protected by PQC), but it would also make DDoS attacks on that day much harder to execute - any in-country IP addresses could be shut down in minutes, while foreign IP addresses wouldn't be allowed to connect to those gateway nodes. I can't estimate the impact of this approach so I wouldn't recommend it, but there may be similar use cases where having your own node on the network could be beneficial.
Final thoughts
I don't expect Worldcoin's integrations in Malaysia will result in much demand on xx Network when postage becomes available. For Malaysia, I wouldn't be surprised if the government mandated that all Worldcoin-integrated apps include various gov-mandated data gathering add-ons.
But what excites me is that similar integrations will sooner or later happen in some other country. A Worldcoin-integrating app developer may also choose to enable xxNetwork-related privacy features. If that sounds unlikely to you, please see the interview with Mario and the voting integration (one of the three grants). Even Malaysia may want to enable anonymity in a Worldcoin voting app and disable it in other domestic Worldcoin applications.
Postage v1.0 may not be able to satisfy all use cases right away. DoS-style attacks by sock-puppet accounts could cause issues even to users of the Premium tier, but xx Network has world-class developers who are no doubt aware of all these things and will make recommendations related to privacy, security, performance and reliability expectations.
Postage v1.0 may become available a few months from now and it is one of the features essential for monetization of xx Network's mixing services.
Other apps rely on donations, subscriptions, or may be VC-backed and don't need to charge just yet.
xx Network is integrated with a blockchain service and very unique in that regard. Rewards - and later postage - are sent and received on a blockchain. For messaging, servers that pass and mix messages are operated by individuals from many countries and they're currently rewarded for their "mixing", but there's only a free tier so rewards aren't as impactful and demand for coins is lower because there aren't real life use cases for it. Postage will improve and better align users' and operators' incentives.
My take:
- Worldcoin in Malaysia won't make xx coin "go to the moon"
- Benefits of xx Network integrations with Worldcoin are real. Potential for adoption is real. When the first integrated implementation happens xx Network traffic could see a significant increase
- All other apps that use xx Network as "transport" could use Premium tier, but currently Worldcoin seems to be the most significant integration.
- Postage won't make xx Network expensive to use. It will make xx Network deliver more value
- Until there's a way to reserve throughput, apps with high reliability expectations should have a way to fallback to Tor or direct access when uptime is more precious than privacy